DMARC ("Domain-based Message Authentication, Reporting and Conformance") is the latest hare-brained scheme to reduce spam and phishing. Like some previous such schemes (I'm looking at you, SPF), it breaks some completely legitimate uses of e-mail.
In this case, it's all about the "From:" line. The "From:" field of an e-mail message is supposed to indicate the author of a message, which can be different from the sender. As RFC 5322 explains
The "From:" field specifies the author(s) of the message, that is, the mailbox(es) of the person(s) or system(s) responsible for the writing of the message. The "Sender:" field specifies the mailbox of the agent responsible for the actual transmission of the message. For example, if a secretary were to send a message for another person, the mailbox of the secretary would appear in the "Sender:" field and the mailbox of the actual author would appear in the "From:" field.
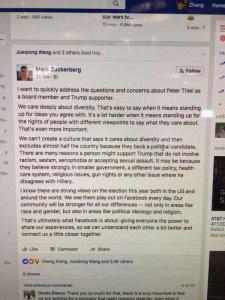
In today's world, the "secretary" is more likely to be some mailing list software. It's quite legitimate for some random internet domain ("example.com") to a mailing list. This list accepts messages from subscribers, such as "some_fake_guy@yah00.c0m"[*], and sends a copy of each such message to each subscriber of the list. The "From:" line of each copy has "some_fake_guy@yah00.c0m", while the "Sender:" is something like "mailing_list_17@example.com".
([*] 0's instead of o's in the address above so it's definitely a bogus address. I'm deliberately picking on Yahoo here.)
The problem is, DMARC lets Yahoo say, "no one but Yahoo! can send an e-mail message with a Yahoo address in the From: line". This breaks the world.
DMARC is what one might call an emerging e-mail security scheme. There's a draft on it at draft-kucherawy-dmarc-base-04, intended for the independent stream. It's emerging pretty fast, since many of the largest mail systems in the world have already implemented it, including Gmail, Hotmail/MSN/Outlook, Comcast, and Yahoo.
...
For a lot of mail, notably bulk mail sent by companies, DMARC works great. For other kinds of mail it works less great, because like every mail security system, it has an implicit model of the way mail is delivered that is similar but not identical to the way mail is actually delivered.
Mailing lists are a particular weak spot for DMARC....
The reason this matters is that over the weekend Yahoo published a DMARC record with a policy saying to reject all yahoo.com mail that fails DMARC. I noticed this because I got a blizzard of bounces from my church mailing list, when a subscriber sent a message from her yahoo.com account, and the list got a whole bunch of rejections from gmail, Yahoo, Hotmail, Comcast, and Yahoo itself. This is definitely a DMARC problem, the bounces say so.
Yes, I spent time last week cleaning up after this. It made me want to punch someone in the nose. I'm going to put that punch away for now, but if I ever meet a system administrator who implemented DMARC in a way that breaks mailing lists, I will be happy to pull it out of storage. Don't let that happen. Just say no to DMARC.